It’s essential to establish policies and procedures to minimize risk in this era of hyper-connectedness and, unfortunately, a burgeoning global cybercrime industry. One specific area on which to focus is your employees. Empowering your employees to recognize common cyber threats can be beneficial to your organization’s computer security. Security awareness training teaches employees to understand […]
Read more
What is TLS? TLS is a protocol that provides a way for two parties to establish a secure communication channel between them. That’s it. But keep in mind that achieving this is no small feat. Look at TLS’ vulnerability history to see how hard it is. TLS makes establishing a secure communication channel possible by providing […]
Read more
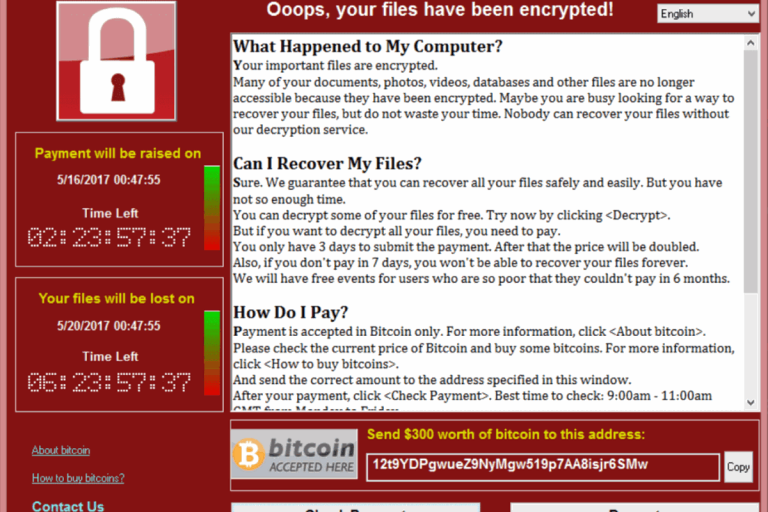
WannaCry, which spanned more than 150 countries, leveraged some of the leaked NSA tools. In May, the ransomware targeted businesses running outdated Windows software and locked down computer systems. The hackers behind WannaCry demanded money to unlock files. More than 300,000 machines were hit across numerous industries, including health care and car companies. Why WannaCry ransomware took down […]
Read more

2018 is coming to a close. So far, here are some of the most noteworthy trends in the ever changing world of Cyber Security The rise of attacks on critical infrastructure — Cases of cyberthreats affecting critical infrastructure made major headlines in 2017. One of the most significant was Industroyer, the infamous malware responsible for the […]
Read more

Netsky and Sasser – Netsky spread via e-mail and Windows networks, creating large amounts of Internet traffic and causing Denial of Service (DoS) attacks. At the time, Netsky and all its variants were believed to have accounted for as many as 25 percent of all computer viruses on the Internet. Sasser replicated by finding other systems with vulnerabilities and forcing […]
Read more
Welcome to WordPress. This is your first post. Edit or delete it, then start writing!
Read more