Frequently Asked Questions
FREQUENTLY
What Is The Methodology
Cyber Threat Susceptibility Assessment (CTSA) is a methodology for evaluating the susceptibility of a system to cyber-attack developed by MITRE. CTSA quantitatively assesses a system’s [in]ability to resist cyber-attack over a range of cataloged attack Tactics, Techniques, and Procedures (TTPs). CTSA consists of the following steps:

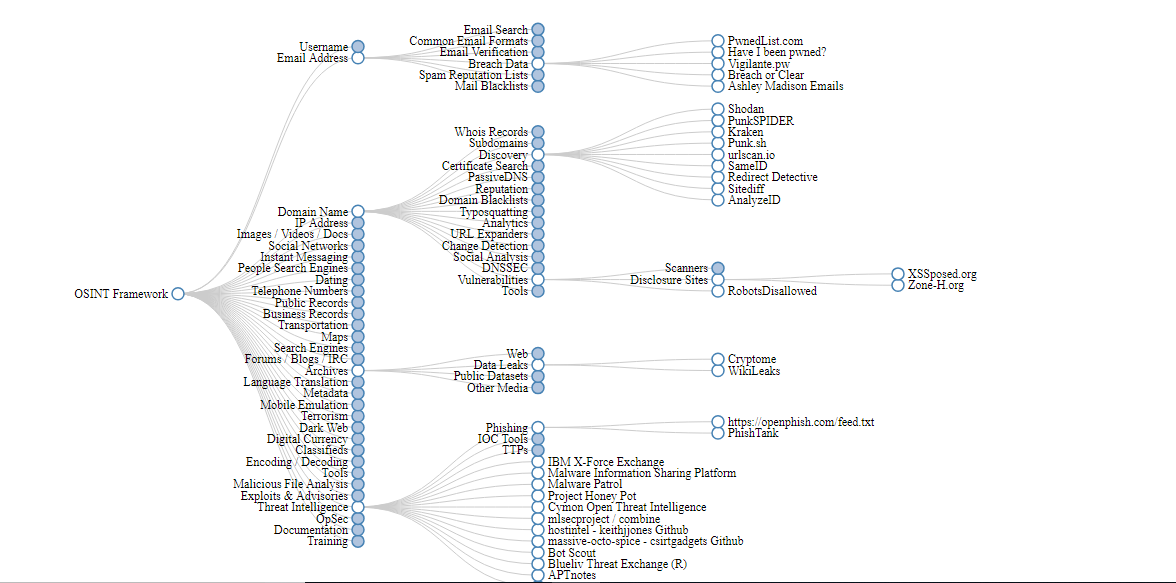
To generate the scorecard, NormShield needs only the company domain. The engine collects the related information from VirusTotal, Passive DNs servers, web search engines and other Internet wide scanners as well as NormShield’s proprietary databases which holds more than 10 billion historic items. The engine searches the database in order to find all IP address ranges and domain names that belong to the company. NormShield uses what is called Open Source Intelligence (OSINT) that is shown below to gather information. The following map shows how hackers can leverage their attack vectors by using OSINT resources like hacker forums, social networks, Google, leaked database dumps, paste sites or even legitimate security services like VirusTotal, Censys, Cymon, Shodan or Google Safe Browsing.
This data is compiled by NormShield into a simple, readable report with letter-grade scores to help identify and mitigate potential security risks. It identifies the risks (CVE / CWE), the risk score of the corresponding vulnerabilities / weaknesses (CVSS / CWSS), attack patterns (CAPEC / FIPS-199 impact level). NormShield also classifies the finding into FISMA Cyber Security Framework Area and Maturity Level, NIST 800-53 Control Family, FIPS-200 Area, NIST 800-37 Process Step. NormShield does all of this without scanning or modifying any of the organization’s business assets.
3rd party risk management is the process of ensuring that the use of external IT service providers and other IT vendors (third parties) does not create unacceptable potential for business disruption or negative impact on business performance. IT 3rd party risk management solutions support enterprises that have to assess, monitor and manage their exposure to risks arising from their use of third parties, which provide IT products and services or have access to enterprises’ client information. Many solutions’ capabilities now extend to identifying, assessing and tracking a vendor’s subcontractors (or fourth-party relationships), a feature that is increasingly important to enterprises.
High-profile failures of IT service providers, increasing rollouts of enterprise risk management programs and third-party access to regulated information are contributing to the demand for 3rd party risk management solutions. Still, however, the biggest driver of vendor risk management is regulatory requirements to address vendor risks, vendor performance, and mandates for the risk monitoring of third parties that can access personal data (such as payment card and protected health information). These mandates include U.S. state-level data breach notification laws, the Payment Card Industry (PCI) standard, privacy and data protection regulations worldwide, and industry-specific regulations in the banking, financial services, healthcare and telecom sectors.
Organizations want assurance that the software products they acquire and develop are free of known types of security flaws. Today, high-quality tools and services for finding security flaws and weaknesses in code are new and the question of which tool/service is appropriate/better for a particular job is hard to answer given the lack of structure and definition in the code assessment industry. Cyber Threat Susceptibility Assessment (TSA) is a methodology for evaluating the susceptibility of a system to cyber-attack developed by MITRE.
NormShield Comprehensive Cyber Risk Scorecard and Rapid Cyber Risk Scorecard are non-intrusive and we don’t use any intrusive vulnerability scanners including Nessus, Netsparker, Acunetix, Nexpose, nmap, openvas etc… In other words, they are passive scan solutions which can be used for any company at any time. As seen in the following diagram, passive scan doesn’t touch to the target company assets instead we find all required data from the internet including search engine caches, archive[.]org, internet-wide scanners, VirusTotal, PassiveTotal, hacker sites, paste sites, deep/dark web etc.

Only the main domain (example.com) name of the target organization.
No need, NormShield will not generate any intrusive or malicious traffic if you requested a scorecard. On the other hand, you may need to whitelist Normshield IP ranges if you are a NormShield Threat & Vulnerability Orchestration customer.
NormShield knowledge base (customers only) includes description, remediation and references of a weakness / vulnerability along with CWE-ID, CAPEC-ID, FIPS-199 impact level, NIST 800-53 control familiy, FISMA maturity level and more.

Rapid Cyber Risk Scorecard (RCRS) is a subset of the Comprehensive Cyber Risk Scorecard (CCRS). RCRS checks about 250+ control items in 10 categories in 60 seconds whereas CCRS checks 500+ items in 20 different categories. Moreover, Comprehensive Cyber Risk Scorecard can estimate the compliance level (NIST 800-53, FISMA, GDPR) of an organazation. On the other hand, Rapid Cyber Risk Scorecard can run in seconds but Comprehensive Cyber Risk Scorecard requires a few hours depending on the company size.
Yes, absolutely. You can get your free scorecard at Rapid Cyber Risk Scorecard page or you can schedule a demo for the comprehensive cyber risk scorecard or threat and vulnerability rchestration.