Get Ready to Kiss Passwords Goodbye
Prepare to bid farewell to passwords! For decades, passwords have been necessary for secure interaction with technology. However, whether you’re an end user, IT professional, or business owner, passwords have caused numerous issues, such as forgetfulness, burdened password resets, password reuse, and susceptibility to phishing scams. It’s become evident that the only way to eliminate these problems is to eliminate passwords entirely. Fortunately, passkeys are rapidly replacing passwords, with Apple’s roll-out of the technology in its iOS 16 and macOS Ventura providing a significant boost.
So what exactly are passkeys? Passkeys use the secure element in laptops, mobile phones, and FIDO2 security keys to store cryptographic secrets. Unlike current passwordless solutions, passkeys utilize the mobile devices you already have, making it simpler for people to adopt them. They also replace both passwords and multi-factor authentication apps, combining multiple factors into a single flow. Passkeys are immune to phishing because your device only provides credentials that match the URL exactly. Passkeys are also unique for each website you visit, making reuse impossible.
Implementing passkeys is relatively straightforward, especially for applications that utilize Single Sign-On (SSO) to your centralized identity provider. However, a plan is necessary to ensure successful and user-friendly implementation. Considerations should be made for user training and support, whether to enroll phones, laptops, or both, and whether USB security keys are necessary for privileged/admin users. Technology considerations include target applications, device operating systems, and legacy devices, while process considerations include onboarding, managing subcontractors and managed service providers, temporary options, and lost devices.
Big tech leaders such as Apple, Google, and Microsoft are working together to make passkeys standard across their ecosystems, which should make the adoption process smoother. At CyberCX, we’re already working with organizations to prepare for this shift and can help you do the same.
Do you wonder what kind of Cybersecurity content is popular? Well, think no ore, here are several ideas that you can use to write blog posts about
How To Prevent Cyber Attacks
check out the full post
here
- The 10 Most Common Cyber Attacks and How To Prevent Them
- Get that hack toolbar off my PC
- Cyber Security for Small to Medium Size Business
- Best Practices for the Corporate World
- Are You At Risk of A Cyber Attack? Here Are The Top 5 Ways To Stay Safer: A blog around cyber attacks along with ways to prevent it.
- Understanding Cyber Attacks: 4 Important Terms to Know: A blog on how to prevent cyber attacks
- Common Cyber Attacks, How To Prevent Them and What You Should Know
- Starting A Small Business? How To Protect Yourself Online
- Some Of The Common Cyber Attacks in The Future
- Tips to Avoid Cyber Attacks
- How To Protect Yourself From Cyber Attacks
- Cyber Attacks A Growing Problem
- Does Your e-mail Contain a Malware? Here Are the Tips on How to Detect If You Have One:
- Common Cyber Security Problems and How to Avoid Them
- Beat Cyber Criminals: A blog about being secure with your family, personal, and business information.
- WIFI Leaves You Vulnerable To Being Hacked! Here’s How To Keep Your Devices Safe!
- Don’t Want To Get Hacked? Check These Out!
- Fighting The Cyber War: A blog about preventing cyber attacks.
- Firewalls and Defenses
- How to Avoid And Prevent Identity Theft
- Why You Should Be Afraid of Hacking
- How to Teach Your Child How to Code
- Infographic: A Concise Guide to Hacking: The infographic shows the basic steps of hacking to help you get started.
- Can A Hacker Be Saved? A blog about hackers and how the world sees them.
- Everything You Need to Know About the Dangerous World of Hacking
- The Most Famous Hack of All Time: A blog about the history and how a hacker got to his ultimate goal.
- How hackers think
- 5 Benefits of Hacking in the Workplace
- The Best Hacking Books of All-time
- The Complete Beginner’s Guide to Hacking
- 7 Tips for Hacking Your Social Media Presence
- Hacking 101: An Introduction to Hacking for Beginners: A blog about hacking for beginners as well as for experienced hackers.
- Internet Hacker’s Guide to SQL Injection: A blog on how to best insert into databases.
- Don’t Be Attacked, Be Defended: A blog with tips on how to protect yourself from hackers and malware.
Here is a good example of what CyberArk job requirements look like:
• CyberArk 10.X, 11.x, 12.x version proficiency and difference of versions
• Hands on experience in CyberArk environment installation, setup, configuration.
• Backup and DR Load balancing setup, setting up failovers between vaults.
• Experience with implementing HA Cluster vaults.
• End to end activities related to version upgrade.
• Windows patching on EPV servers.
• Integrating various platforms with CyberArk such as Windows servers, UNIX servers, Databases and networking Devices like Oracle, SQL databases, SSH Keys, HSMs, ERP solutions, RPA solutions and other applications.
• Experience in Safes, Platforms, Accounts, Platforms, Connector in the CyberArk environments.
• CPM policies management or redistribution.
• Perform health check monitoring on all CyberArk severs to ensure consistent availability of system to end user.
• Integration with infrastructure systems like logging, monitoring.
• Assess and Analyze the environment to detect critical deficiencies and recommend solutions for improvement, target architectures and a roadmap
• Experience in the use of CyberArk PACLI to automate tasks related to user and safe management.
• Define PAM Governance Frameworks and PAM Requirements
• Privileged User account administration of various Windows and UNIX accounts using CyberArk components.
• Experience maintaining and troubleshooting complex CyberArk environments and component-based issues.
• Auditing Accounts and work on various reports, user’s server login issues and user permission issues as per requirements.
• Define standard operating procedures (SOPs) and implementation /deployment plans for privileged account security solutions and identity governance solutions
• Implementing the Password Upload Utility.
• Experience in collaboratively resolving complex issues with CyberA
• Play active role in the execution of the project and demonstrate strong technical leadership.
• Lead and mentor team members, including coaching junior engineers and architects.
• Collaboration with stake holders
• Understanding of SSH and Windows RDP.
• Experience in systems like Service Now, Radius, SAML, LDAP, Active Directory, SailPoint
• SIEM systems, ticketing systems such as Remedy, ServiceNow, enterprise monitoring and alerting using SNMP
Here are some common tasks and responsibilities associated with role of CyberArk Administrator:
JOB DESCRIPTION:
Seeking a CyberArk administrator responsible for managing CyberArk production environment managing more than twenty thousand accounts.
Highly motivated candidates for CyberArk Administrator position with networking background and or similar educational background.
This position performs Administration & Support for a CyberArk deployment as well as other related systems or technologies required to sustain and maintain capabilities of the services.
Successful candidate must possess and be able to demonstrate technical skills and engineering attitude for success, dedication and commitment.
TASK AND RESPONSIBILITIES:
- Troubleshooting system and application accounts in a diverse systems/application architecture.
- Demonstrated experience with Administering a CyberArk Enterprise Password Vault – deployment and detailed knowledge of the following CyberArk components confirmed by related work experience:
- PSM, CPM, AIM • PVWA, Vault Administration, Disaster Recovery
- Maturity and discipline to follow established processes and detailed technical procedures to ensure consistency and predictability • Demonstrated experience with developing and following processes, templates, instructions, presentations and progress measurement material.
- Demonstrated ability to work on virtual teams and must possess good interpersonal skills
- Must be familiar with password rotations, password malfunctions, account creations, account changes, accounts integrations, maintaining/creating new safes, and CyberArk policies.
- Further responsibilities include managing EPV(Enterprise Password Vault) with respect to information/systems security and identity/access management.
- Candidates may be required to provide end-user training and CyberArk infrastructure management.
- Create Documents for end users.
· What is CyberArk?
- Ans: CyberArk is a data security organization providing Privileged Account Security. The organization’s innovation is used fundamentally in the monetary administrations, energy, retail and medical care markets. It has the greater part of fortune 500 in its client’s rundown. The settlement of CyberArk is in Petah Tikva, Israel and the headquarters is in Newton, Massachusetts.
· What are the basic functions of Cyberark?
- Ans: CyberArk’s essential function is organized by CyberArk EPV. It is one of the components of CyberArk’s security arrangement of the privileged record. CyberArk EPV, otherwise called CyberArk Enterprise Password Vault is intended to find, secure, pivot and control admittance to private record passwords utilized to get to any framework all through the association in its Information Technology climate.
· What is OPM?
- Ans: OPM is an abbreviation of On-Demand Privileges Manager. This is accessible for both Linux/Unix and for Windows. The clients are permitted to be restricted to orders with access which is directly from those of the adaptable policy of OPM.
· Define Privileged Session Manager.
- Ans: CyberArk’s key module is called PSM. It is answerable for the protection of the availability of every single privileged client and its exercises at database and OS stages. This also observes the clients’ admittance to the centralized computer locales. Private Session Manager permits a single focus of control to avail. It checks every keystroke and tallies each mouse snap and makes sure to not allow any malware to get to enter the target framework.
· Who is a privileged user?
- Ans: Any framework’s privileged client has altogether more potential in that framework and these possibilities are bigger than those distributed to the greater part of different clients. It is more inclined to be hacked. The records are ignored that open them to large dangers. It’s basic for programmers to get to these assault focuses for strengthening privileged admittance into the organization. The admin itself utilizes the record of privilege to create alterations in various different apps and information bases. The accounts can be utilized to compare with different administrations of the web and are in danger of being controlled by the interlopers.
· What is CyberArk viewfinity?
- Ans: Viewfinity is the EPM ( Endpoint Privilege Manager ) of CyberArk having improved security measures. CyberArk Viewfinity permits the foundation to implement minimal strategies of privilege for the admins of the framework and business, hoisting the advantages for operating the approved apps. It aids the servers to get hindrance from unintentional harms and furthermore decreases the isolated obligations of regulators on servers. The environ gets safeguarded from being invaded through threatening apps by allowing unrecognized apps to operate independently in experimental mode.
· What does CyberArk PSM’s web form ability mean?
- Ans: Using a bunch of conditions, PSM connectors could be incorporated into online applications. Naturally PSM web capacity just covers html login page with structure id, input structure for client/ password and button name trait.
· .What is an AIM?
- Ans: Application Identity Manager, an application dependent on Linux and Windows that encourages admittance to privileged passwords and deletes the requirement to hard code the plaintext passwords in contents, apps or setup records. Likewise with all different qualifications stored in the EPV, AIM passwords are put away, logged, and handled unequivocally. It is isolated into two parts: a provider that safely recovers and stores passwords and gives quick admittance to the application; and the SDK that gives a bunch of APIs to .NET, Java,CLI15, COM14, and C/C++. In the assessed variant, the AIM Provider for Windows and SDK have been rejected.
· What is Password Vault Web Access (PVWA) Interface?
- Ans: Password Vault Web Access (PVWA) Interface is a web interface that gives a solitary console to mentioning, availing, and handling privileged record qualifications transferred all through the venture by both clients and framework heads. PVWAs dashboard encourages clients to gain an outline of the functions in PAS Solution.
· .If CyberArk vault user changed his Active Directory password what will happened with his CyberArk account?
Ans: Nothing will happen, If CyberArk uses LDAP authentication
· .Which Component used on all Cyberark solutions?
· .What are the CyberArk Vault protection layers?
- Ans:Following are the CyberArk Vault Protection Layers:
- Firewall & Code-Data Isolation
- Encryted Network Communication & Visual Security Audit Trail
- Strong Authentication & Granular Access Control
- File Encryption & Dual Control Security
· .About privilege account request/approval or also known as dual control, which following statement is false?
- Requester will receive email notification upon approval
- Approvals is working in hierarchy
- Request can be set for a specific time & date
- Approvals is working in minimum number of approvers
- Maximum request access for 5 consecutive days
- Ans:Approvals is working in hierarchy
· .CyberArk’s PIM stands for?
- Ans:Privilege Identity Management
- What is CyberArk Vault Dual Control ?
- Confirmation needed to open a safe
- Confirmation needed to retrieve files
- Confirmation needed to open a safe and to retrieve files
- At least 1 safe owner who are authorized to confirm request
- All of above
- Ans:Confirmation needed to open a safe
- How long CyberArk Vault will kept deleted object until it reach true deletion stage?
- Ans:30 days
- What are User Accounts Enabled by Default?
- Administrator
- Auditor
- Master
- Backup
- None of above
· Does CyberArk PSM has web form capability?
· What you need to have to enable auto password reconciliation policy?
- Ans: Following should enable for auto password reconciliation policy in cyberark
- Enable Password reconciliation for specific policy
- Additional account on target server with sufficient rights
- Automatic password verification shoud enable
- Enable password reconciliation when password is unsync
What are the components of CyberArk?
Privileged Access Security Solution Architecture
The CyberArk Digital Vault is the most secure place in the network where sensitive data can be stored. …
The Password Vault Web Access Interface. …
PrivateArk Administrative Interfaces. …
The Central Policy Manager. …
Privileged Session Manager. …
Privileged Session Manager for SSH. …
Privileged Session Manager for Web.
What is CyberArk used for?
CyberArk is predominantly a security tool used for the security of privileged accounts through password management. It protects the privileged accounts in the organizations by way of maintaining the passwords automatically. It logs and audits privileged account use, and will automatically generate a new password every time someone “checks out” a password.
Why CyberArk is required?
Why Your Business Needs PSM
Integrate with ticketing systems and change controls. Control access to servers with policy-based access control. Make restrictions on the privileged session duration. Notices privileged sessions with the ability to terminate with suspicious sessions and interact with them.
Who are CyberArk competitors?
Microsoft Azure Active Directory, HashiCorp Vault, Thycotic Secret Server, and BeyondTrust Privileged Remote Access are the most popular alternatives and competitors to CyberArk Privileged Access Security Solution.

It’s essential to establish policies and procedures to minimize risk in this era of hyper-connectedness and, unfortunately, a burgeoning global cybercrime industry. One specific area on which to focus is your employees.
Empowering your employees to recognize common cyber threats can be beneficial to your organization’s computer security. Security awareness training teaches employees to understand vulnerabilities and threats to business operations. Your employees need to be aware of their responsibilities and accountabilities when using a computer on a business network.
New hire training and regularly scheduled refresher training courses should be established in order to instill the data security culture of your organization. Employee training should include, but not be limited to:
Responsibility for Company Data
Continually emphasize the critical nature of data security and the responsibility of each employee to protect company data. You and your employees have legal and regulatory obligations to respect and protect the privacy of information and its integrity and confidentiality.
Document Management and Notification Procedures
Employees should be educated on your data incident reporting procedure in the event an employee’s computer becomes infected by a virus or is operating outside its norm (e.g., unexplained errors, running slowly, changes in desktop configurations, etc.). They should be trained to recognize a legitimate warning message or alert. In such cases, employees should immediately report the incident so your IT team can be engaged to mitigate and investigate the threat.
Passwords
Train your employees on how to select strong passwords. Passwords should be cryptic so they cannot be easily guessed but also should be easily remembered so they do not need to be in writing. Your company systems should be set to send out periodic automatic reminders to employees to change their passwords.
Unauthorized Software
Make your employees aware that they are not allowed to install unlicensed software on any company computer. Unlicensed software downloads could make your company susceptible to malicious software downloads that can attack and corrupt your company data.
Internet Use
Train your employees to avoid emailed or online links that are suspicious or from unknown sources. Such links can release malicious software, infect computers and steal company data. Your company also should establish safe browsing rules and limits on employee Internet usage in the workplace.
Email
Responsible email usage is the best defense for preventing data theft. Employees should be aware of scams and not respond to email they do not recognize. Educate your employees to accept email that:
- Comes from someone they know.
- Comes from someone they have received mail from before.
- Is something they were expecting.
- Does not look odd with unusual spellings or characters.
- Passes your anti-virus program test.
Social Engineering and Phishing
Train your employees to recognize common cybercrime and information security risks, including social engineering, online fraud, phishing and web-browsing risks.
Social Media Policy
Educate your employees on social media and communicate, at a minimum, your policy and guidance on the use of a company email address to register, post or receive social media.
Mobile Devices
Communicate your mobile device policy to your employees for company-owned and personally owned devices used during the course of business.
Protecting Computer Resources
Train your employees on safeguarding their computers from theft by locking them or keeping them in a secure place. Critical information should be backed up routinely, with backup copies being kept in a secure location. All of your employees are responsible for accepting current virus protection software updates on company PCs.
What is TLS?
TLS is a protocol that provides a way for two parties to establish a secure communication channel between them.
That’s it.
But keep in mind that achieving this is no small feat. Look at TLS’ vulnerability history to see how hard it is.
TLS makes establishing a secure communication channel possible by providing three key services:
- Confidentiality: ensures that data exchanged between peers is kept secret from third-parties. This is especially important for sensitive data, like passwords, credit cards, and the embarrassing contents of our shopping carts. Confidentiality is the characteristic that is most commonly associated with TLS, and its purpose is usually well understood;
- Integrity: makes sure that data transmitted between peers is reliable and not tampered with during transit. Note that in the context of TLS, “integrity” refers to message authentication;
- Authentication: ensures that clients communicate with legitimate servers. This is fundamental for assuring both confidentiality, and integrity, by providing trustworthy keying material for encryption and message authentication. Note that authentication and integrity are always important, whether the transmitted data is confidential or not. Optionally, TLS can also be used to authenticate clients, e.g. through client certificates, but this is less common;
Why do we need TLS?
One common criticism against TLS is that “TLS is slow”; for the vast majority of use cases, it is a misconception, even more so in TLS 1.3.
Another argument is that “All information on my website is public, so I do not need TLS”. A service providing public information may not require confidentiality, but authentication and integrity should never be optional. Otherwise, a user visiting an unprotected website has no guarantees about the authenticity of the information contained on it. The user may be attacked or, at best, annoyed by a potential man-in-the-middle — think Wi-Fi networks, or less ethical ISPs.
Some possible attack scenarios follow.
- Subtly change a small, but critical, piece of information on a website. Such as a bank account number, cryptocurrency wallet address, phone number, email, and others;
- Launch an “opportunistic cingryptojack” attack by injecting cryptocurrency mining code on the original webpage;
- Redirect the victim to a phishing page to steal their credentials;
- Inject ads and analytics/tracking javascript.
A brief TLS timeline
In the beginning, there was SSL 1.0. Not much public information is available. According to one source, several design flaws, such as missing data integrity and no replay protection, prevented SSL 1.0 from seeing the light of day;
SSL 2.0, the first public version, is eventually released in March 1995, as part of Netscape Navigator 1.1 browser. Several security issues are found, such as cipher downgrade and length-extension attacks;
SSL 3.0 is released in March 1996, with Netscape Navigator 2, fixing several vulnerabilities found in SSL 2.0;
TLS 1.0, a.k.a. SSL 3.1, is released in January 1999, after a standardization effort by the IETF. It is an incremental evolution over SSL 3.0, bringing no dramatic changes;
TLS 1.1 is released in April 2006. It includes mitigations to attacks on CBC ciphers. One particular change, explicit initialization vectors, will eventually prevent BEAST, five years into the future;
TLS 1.2 is released in August 2008. Changes include support for authenticated encryption with associated data (AEAD) ciphers, like AES-GCM, and stricter protocol validations;
TLS 1.3 is released in August 2018. There are many major differences from TLS 1.2, to the point that some believe it should be called TLS 2.0. We will briefly cover them below.
What is new in TLS 1.3
1. Perfect-forward secrecy is now mandatory.
2. TLS 1.3 comes with a redesigned, safer and faster 1-RTT handshake. In TLS 1.3, after the initial handshake messages, everything is encrypted. This means that even server certificates are encrypted.
3, A ton of stuff was removed: renegotiation, compression, and many legacy algorithms: DSA, RC4, SHA1, MD5, CBC MAC-then-Encrypt ciphers
4. Supposedly lot more reselient against downgrade attacks
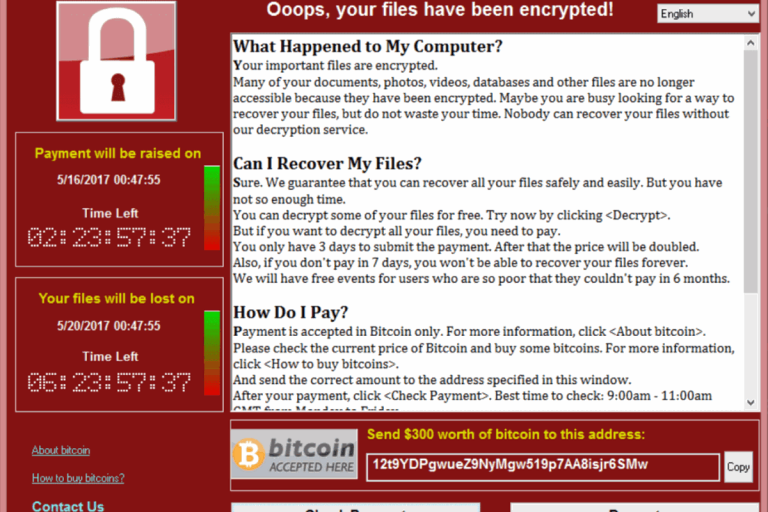
WannaCry, which spanned more than 150 countries, leveraged some of the leaked NSA tools. In May, the ransomware targeted businesses running outdated Windows software and locked down computer systems.
The hackers behind WannaCry demanded money to unlock files. More than 300,000 machines were hit across numerous industries, including health care and car companies.
Why WannaCry ransomware took down so many businesses? – running “legacy software,” or old, outdated technology that no longer receives software updates
The vulnerability WannaCry exploits lies in the Windows implementation of the Server Message Block (SMB) protocol. The SMB protocol helps various nodes on a network communicate, and Microsoft’s implementation could be tricked by specially crafted packets into executing arbitrary code.
Even if a PC has been successfully infected, WannaCry won’t necessarily begin encrypting files. That’s because, as noted above, it first tries to access a very long, gibberish URL before going to work. If it can access that domain, WannaCry shuts itself down. It’s not entirely clear what the purpose of this functionality is. Some researchers believed this was supposed to be a means for the malware’s creators to pull the plug on the attack. However, Marcus Hutchins, the British security researcher who discovered that WannaCry was attempting to contact this URL, believes it was meant to make analysis of the code more difficult.
Ironically, the patch needed to prevent WannaCry infections was actually available before the attack began: Microsoft Security Bulletin MS17-010, released on March 14, 2017, updated the Windows implementation of the SMB protocol to prevent infection via EternalBlue. However, despite the fact that Microsoft had flagged the patch as critical, many systems were still unpatched as of May of 2017 when WannaCry began its rapid spread.

2018 is coming to a close. So far, here are some of the most noteworthy trends in the ever changing world of Cyber Security
- The rise of attacks on critical infrastructure — Cases of cyberthreats affecting critical infrastructure made major headlines in 2017. One of the most significant was Industroyer, the infamous malware responsible for the 2016 attack on Ukraine’s power grid. Attacks on critical infrastructure can also affect much more than just the power grid and could include the defense and healthcare sectors, water, transportation, and both critical manufacturing and food production. Organizations are working hard on security but ever-changing conditions mean that threats are likely to continue through 2018.
- Supply chain issues — Large companies are waking up to the threat of cyberattacks with security teams receiving increased backing to improve measures. But SMEs continue to struggle with these new concerns, and since they may also supply goods and services to larger organizations, security gains are often negatively impacted. These types of supply chain problems affected the entertainment industry earlier in 2017; among the incidents included was the attempted extortion of Netflix over a new season of the series “Orange Is the New Black.” This should remind us that supply chain security can affect any industry, and is likely to continue in 2018.
- Increased cooperation between law enforcement and cybersecurity experts — Malware research has proved useful to law enforcement in the war on cybercrime. A key example is a recent collaboration between ESET, Microsoft, and law enforcement agencies, including the FBI and Interpol, working together to take down a major botnet operation known as Gamarue. Increased cooperation will lead to more arrests and fewer active cybercriminals. As authorities continue to gain experience working with private cybersecurity specialists, we can look toward further successful investigations and a potentially safer 2018.
- Democracy hack: Can electoral processes be protected? Recent elections have raised numerous cybersecurity questions – the most important being to what extent a cyberattack can influence the electoral process. As discussed in the report, evidence suggests we must look toward a hybrid system using both paper and electronic records if we are to mitigate fraud by cybercriminals.
- Our privacy in the new age of tech — Data is the new currency, with consumers expecting to enjoy software at little or no cost. This has led vendors to enter the data-collection business, increasing the risks connected with data privacy. Advancements in IoT can lead in a similar direction with every device capable of telling a story and producing a full picture of the user’s life if multiple connected devices are combined.